Qualys recently found not one, not two, not three but literally five vulnerabilities inside of a tool that is installed on every single ubuntu server by default that leads to direct privilege escalation.
Those vulnerabilities are identified by CVE-2024-48990, CVE-2024-48991, CVE-2024-48992, CVE-2024-10224, and CVE-2024-11003.
They all happen inside of a package called needrestart which is written in perl and ostensibly exists to see if the system or services on said system need to be restarted after an update -- for instance after running 'sudo apt-get install mynewtoy' - something a lot of people will be doing just to "mitigate" this set of vulnerabilities. Re-read that again.
There are so many things wrong with this that it makes you want to pull your hair out and this type of problem is totally preventable.
I was going to write a tweet about this and be done with it but this is precisely the type of stupidity that happens on almost every single cloud server today. It is not because the end users are dumb - it is because they don't know of tools that exist that allow them to not have to deal with these issues.
Just to be clear - I don't have a problem with the authors of this particular application. I don't have a problem with debian/ubuntu maintainers/employees. I have a problem with the idea that we should be provisioning servers that are explicitly designed to run many different applications written in many different languages by many different users when we have the technology to not do that.
It it an architectural and education problem.
Let me explain. Let us suppose you write in Go or Rust or Java or some other random language. Does it make any sense for you to have a perl interpreter or a python interpreter or a ruby interpreter on that same instance?
You might say - well this program requires perl - but - that's doing it the 'old way' - the way we've done it in the past - it's not something you have to do anymore. Unikernels allow you to sidestep this.
Unikernels deploy a single application for a single language. There is no "shelling out" to another language. There aren't a half dozen different interpreters and their associated libraries hanging around. The system quite literally does not have support for you to do this so it's less like a wolfi/alpine and it's more like - you quite literally can't do that. If you want to update your application you just simply push a new version of it - in this world the application and the instance become one discrete unit. This approach eliminates entire classes of weaknesses such as CWE-77 and severely limits many others.
This set of vulnerabilities really rubbed me the wrong way and the more I read into it the worse it seemed to get.
First off - Perl is so old it isn't even named Perl anymore! The newest version of Perl is now called Raku because I guess it got too different for the old-schoolers from 1987.
Second off - if I go boot a ubuntu t2.small on AWS right now - why the hell is this thing running? I only have one thread to work with - it should be running my payloads - not some "updater" process running perl that wants to shell out to ruby and python and god knows what else. This is a cognitive dissonance that most of the world that rides on AWS, GCP, Azure or vSphere, Proxmox, etc. has not realized yet.
Something is Deeply Wrong with the Servers
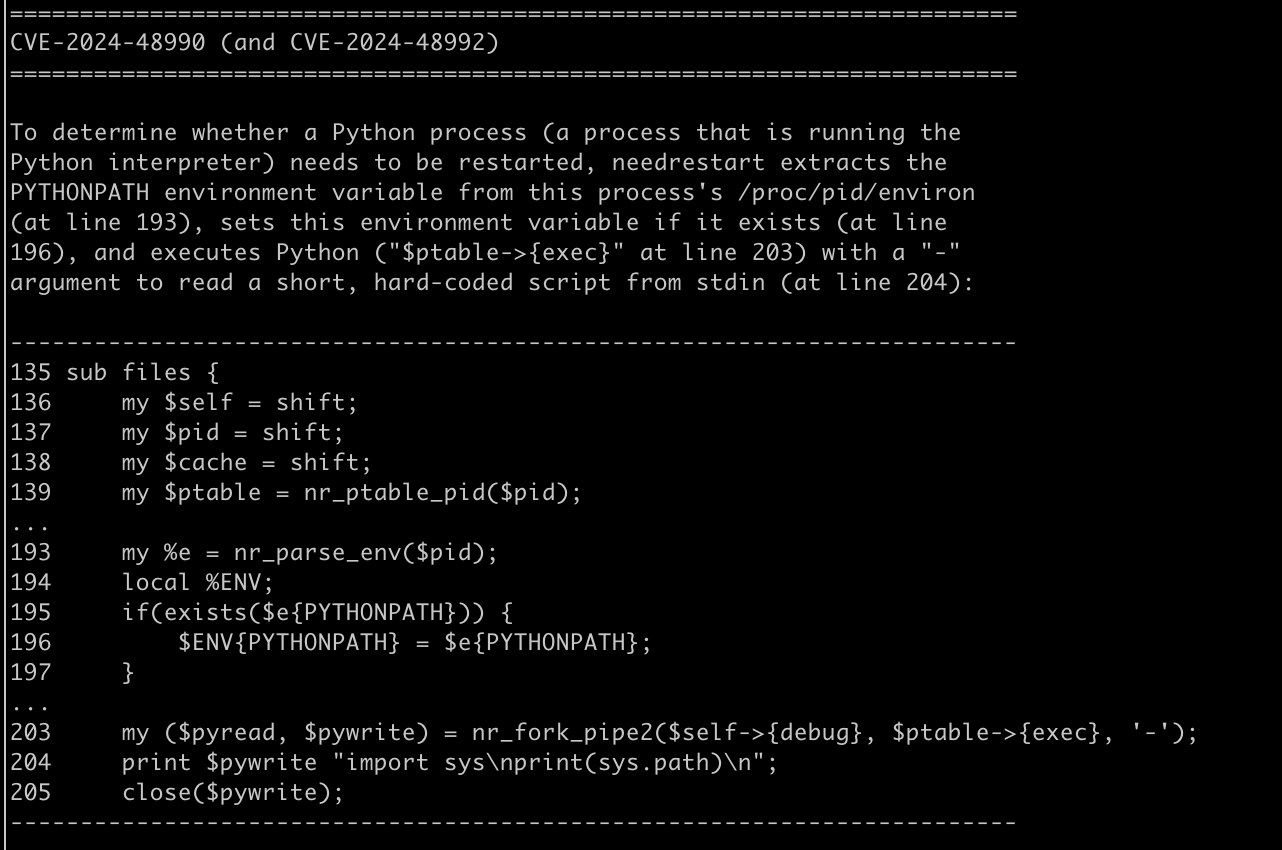
This vulnerability is executed by by tricking the needrestart program into using an attacker controlled ruby or python interpreter through the use of RUBYLIB or PYTHONPATH env vars. The Qualys researchers even quip that they didn't spend too much time looking at the ruby vector cause it wasn't installed by default on the ubuntu server (eg: the python interpreter was!).
You know what is really crazy about this stupid set of vulnerabilities?
It isn't the first time this happened to the same piece of software with the same proposed mitigation as show in CVE-2022-30688.
$nrconf{interpscan} = 0;
Just disable the interpreters they say. Well clearly that didn't work last time did it?
Fourth, this set of vulnerabilities has been sitting in needrestart for over 10 years now!
Finally, if one actually consults the readme of this project you might quickly come to the same conclusion as me - there are a lot more vulns/cves coming out for this can of worms.
Hollywood and the government want you to believe that the worst cybersecurity problems are 1337 h4x0rz from planetZ and everyone is putting up a valiant fight. Yeh - that's bullshit. The tools and processes that organizations the world around are using are totally inadequate.
This is the part where I might offer you a rule to add to a scanner to let you know if one or more of your systems is vulnerable - yeh ... I'm not going to do that.
The idea of a server needs a complete restart, a complete overhaul. If you're running on the cloud you owe it your team to check out running unikernels.
Stop Deploying 50 Year Old Systems
Introducing the future cloud.